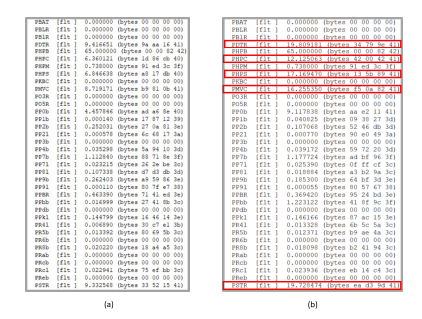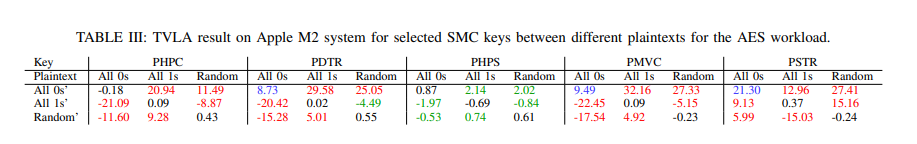
The research focuses on exploiting the System Management Controller (SMC) on Apple’s M1/M2 platforms. The SMC, which provides access to on-chip power meters through a software interface, is found to have data-dependent power consumption. The researchers demonstrate that an unprivileged user mode application can leverage this to successfully recover bytes from an AES encryption key from a cryptographic service supported by a kernel mode driver in MacOS.
The implications of this research are significant. It shows that software-based power side-channel attacks are an industry-wide problem, affecting various architectures. The research also highlights the challenges in developing a suitable mitigation plan. The findings underscore the need for careful consideration of software interfaces for modern on-chip power management systems, as they can potentially be exploited for malicious purposes.
Publication date: June 28, 2023
Project Page: N/A
Paper: https://arxiv.org/pdf/2306.16391.pdf